Bug Bounty Programs May Sound Great, But Aren't Always Handled Well
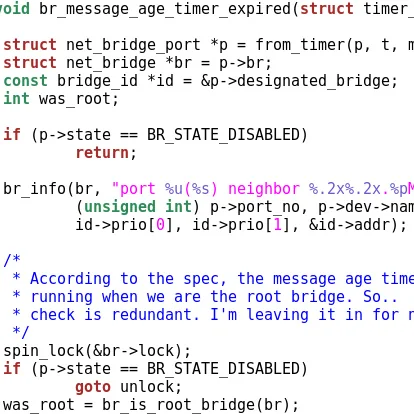
Adam Zabrocki is the security researcher who ultimately discovered this Intel Linux "i915" kernel graphics driver vulnerability that was made public earlier this month. A potential out of bounds memory access could lead to an escalation of privileges for local users. He discovered the problem last year but then submitted it to Google as part of their Chrome OS bug bounty program since Intel graphics are commonly used with Chromebooks. He ultimately got the run-around from Google and Intel while in the process of working out the i915 kernel driver fix wasn't even originally attributed as reporting the bug.
Zabrocki wrote a lengthy blog post about the challenges in dealing with bug bounties from his experience working with Google and Intel. It's a long read but quite intriguing and outlined an area of bug bounty handling that I wasn't aware of.
Among the lessons learned that were shared by Zabrocki:
"My experience with bug bounties was much worse than I expected. Especially Google’s attitude of being silent forever until things went horribly/obviously wrong. Then, they tried to put the responsibility for everything on Intel and convince me that it was not their problem even though the bug was reported to them, and that they were handling the communication very well(!). As a researcher, what can you do? Nothing.
Intel screwed up badly, but they tried best to fix what they messed-up (and what was still possible to fix at that point). Contrary to Google’s attitude, Intel didn’t blame anyone, and they didn’t try to convince me that they were doing their best and they were not dismissive.
It is worth mentioning that Intel officially apologized for how this case was handled: “(…) We would like to apologize for the way this case has been handled. We understand the back and forth with us has been frustrating and a long process. (…)“. However, nothing like that happened on Google’s part.
If this bug was really valuable from the exploitability perspective, it looks like still the best option is to dust off the old broker contacts (if we leave the moral questions aside). They never ever failed so much (at least that’s my experience), even though they are not ideal as well.
Btw. To be fair, there are also positive examples of bug bounty programs"
Read more about Adam's bug bounty experience on his blog.
13 Comments

