Originally posted by kpedersen
View Post
Announcement
Collapse
No announcement yet.
Google Proposes New mseal() Memory Sealing Syscall For Linux
Collapse
X
-
For many years Apple was even less secure than Windows. Linux and OpenBSD are leaders when comes to security. They're collaborating with each other. Nothing else come even close. Windows, macOS, FreeBSD are the least secure operating systems. Windows is insecure by design, Apple OS was always a toy and had broken security for years (ASLR afair). When comes to 'catching up' it seems everyone is trying to catch up with Linux. Linux had incomplete ASLR implementation in 2001, OpenBSD got full one in 2003, Apple in 2011 (and it was broken afaik), Windows since Windows 10 and it wasn't enabled by default. Next time get your facts straight.Last edited by Volta; 18 October 2023, 03:40 AM.
- Likes 2
-
I'm happy that we have the freedom of choice. OpenBSD puts security first. Linux puts usability first.Originally posted by kpedersen View Post
Good to see Linux trying to catch up with security ideas though. Always surprising to see Apple ahead of the game (for OpenBSD it is obviously expected since security is one of its main focuses).
Micro: If I am maintaining my own hardware and I have restricted access to very few users/services then I would use OpenBSD on an AMD64 system*.
Macro: If I am using multiple cloud instances with many users and services that has different levels of access I would prefer using Linux over BSD. AWS seems to be doing the same if you look at Lambda or Fargate.
FreeBSD and OpenBSD are not maintaining architectures other than AMD64. There are many known vulnerabilities that are not planned to be fixed ever and their docs are even outdated: https://wiki.freebsd.org/Speculative...ulnerabilities
*My first choice would actually be custom ISA on a custom OS but that's out of the scope here.
Comment
-
Since Vista - 2007.Originally posted by Volta View Post
Windows since Windows 10 and it wasn't enabled by default. Next time get your facts straight.
Of course it is enabled by default and you are lying as usual.Windows 10 and it wasn't enabled by default.
You have some serious disorders.
Go to therapy or something. Maybe confabulation can be cured. I don't know.Last edited by HEL88; 18 October 2023, 08:39 PM.
- Likes 1
Comment
-
The back and forth between Jeff Xu and Theo goes back and forth several times. But Theo basically gets to the point that he's (politely) losing patience and just lays it out bare faced: This proposed syscall isn't for the benefit of the Linux community, it's for Chrome (Google) and only for Chrome - and it's not even a well considered change. He doesn't go QUITE so far to say it, but basically I can see Theo thinking this is the Chrome team trying to push its will on everyone else without bothering to negotiate in good faith. OpenBSD as a group has experienced this in the past with mimmutable() - which Theo says was specifically designed to do what Jeff is currently proposing, but were ignored entirely - presumably because of NIH syndrome.
- Likes 1
Comment
-
FreeBSD monitors what OpenBSD does and imports relevant changes. Why do you think FreeBSD belongs in the "low security" bracket?Originally posted by Volta View Post
For many years Apple was even less secure than Windows. Linux and OpenBSD are leaders when comes to security. They're collaborating with each other. Nothing else come even close. Windows, macOS, FreeBSD are the least secure operating systems. Windows is insecure by design, Apple OS was always a toy and had broken security for years (ASLR afair). When comes to 'catching up' it seems everyone is trying to catch up with Linux. Linux had incomplete ASLR implementation in 2001, OpenBSD got full one in 2003, Apple in 2011 (and it was broken afaik), Windows since Windows 10 and it wasn't enabled by default. Next time get your facts straight.
Comment
-
MS told me you're a liar:Originally posted by HEL88 View PostOf course it is enabled by default and you are lying as usual.
I've been using it for quite a while now, it caused no problems or errors with any legitimate programs, games, anti cheat systems etc other than with some..
've been using it for quite a while now, it caused no problems or errors with any legitimate programs, games, anti cheat systems etc other than with some "custom" made portable programs. it's Off by default, when you turn it on, you will have to restart your device. An overview of software and firmware threats faced in the current security landscape, and the mitigations that Windows 10 offers in response to these threats.
An overview of software and firmware threats faced in the current security landscape, and the mitigations that Windows 10 offers in response to these threats.
Windows 10 applies ASLR holistically across the system and increases the level of entropy many times compared with previous versions of WindowsYou don't have to share with me what your friends are telling to you. Just do it.You have some serious disorders.
Go to therapy or something. Maybe confabulation can be cured. I don't know.
P.S. when comes to Vista it had something that their laughable marketing called ASLR. The truth is It had nothing common with ASLR.Last edited by Volta; 20 October 2023, 05:35 PM.
- Likes 1
Comment
-
Theo de Raadt begs to differ:Originally posted by unwind-protect View Post
FreeBSD monitors what OpenBSD does and imports relevant changes. Why do you think FreeBSD belongs in the "low security" bracket?
Basically, it is 10 years of FreeBSD stupidity. They don't know a thing about security. They even ignore relevant research in all fields, not just from us, but from everyone.He said this code was added in 2003. "Like I say, it was using the same method of passing entropy into the bottom of the smoothing subsystem. We don't consider it better than mouse movements. Linux is also using an un-biasable method like us."
"Now we all discover that FreeBSD has been doing it wrong. It's not as if they operate in a closed source world, and couldn't have looked at what others did. They must have chosen a few years ago to do this wrong, intentionally.
"Perhaps that decision was made by their Californian developers, the ones who work fairly close to that NSA building.
"And now we see rah-rah articles apparently praising them for this departure from a poor method, almost as if that is innovation."
Comment
-
You confuse stuff. Most important ASLR is for memory allocations - and that one is always on.Originally posted by Volta View Post
MS told me you're a liar:
I've been using it for quite a while now, it caused no problems or errors with any legitimate programs, games, anti cheat systems etc other than with some..
 An overview of software and firmware threats faced in the current security landscape, and the mitigations that Windows 10 offers in response to these threats.
An overview of software and firmware threats faced in the current security landscape, and the mitigations that Windows 10 offers in response to these threats.
You don't have to share with me what your friends are telling to you. Just do it.
P.S. when comes to Vista it had something that their laughable marketing called ASLR. The truth is It had nothing common with ASLR.
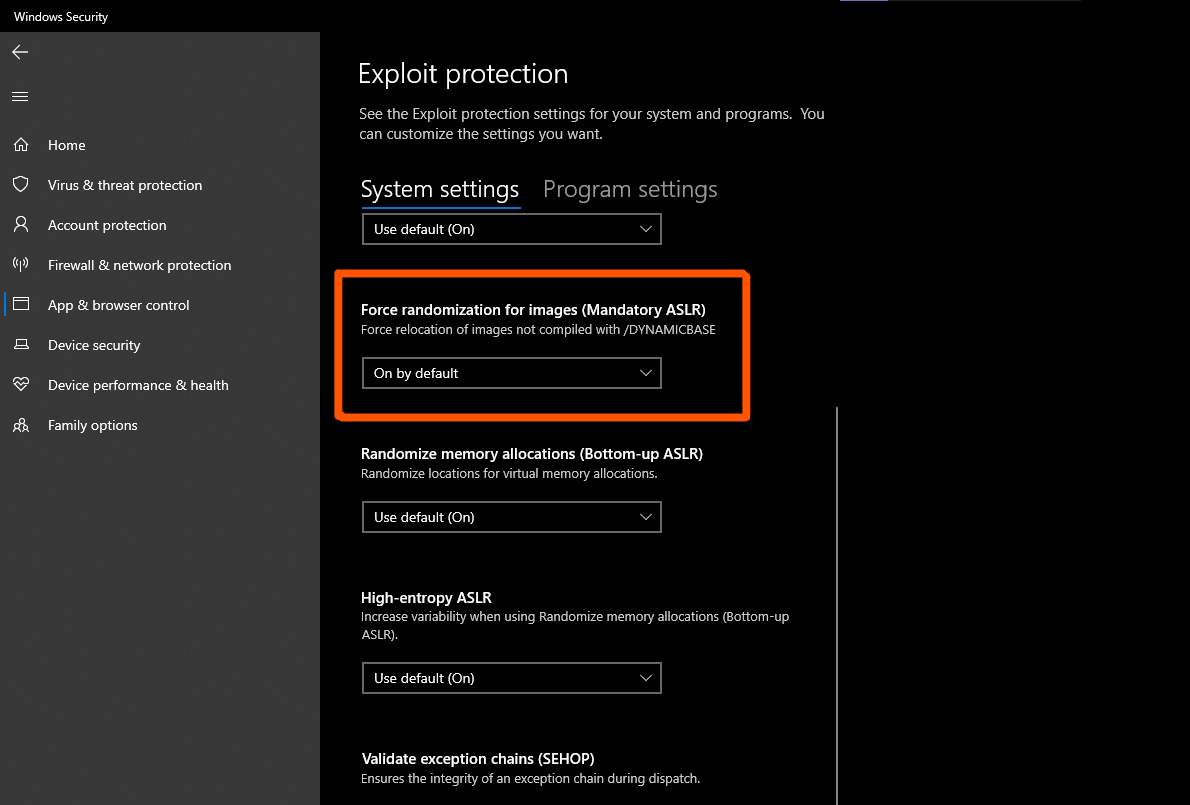
1st. Yes ASLR for base adress of executable is not forced. But Microsoft since like 2007 by default uses /dynamicbase flag on all builds from their tools. If flag is set, ASLR mandatory is on, and since ASLR protects against exploits done in popular programs, those popular programs have /dynamicbase flag on. The reason why it is not default is because some programs not built with that flag on can crash + stuff from older systems. MS actually takes care a lot on backwards compability.
2nd. Weakness of ASLR in windows mostly is about 32 bit versions of windows.
It was noted in February 2012[37] that ASLR on 32-bit Windows systems prior to Windows 8 can have its effectiveness reduced in low memory situations. A similar effect also had been achieved on Linux in the same research. The test code caused the Mac OS X 10.7.3 system to kernel panic, so it was left unclear about its ASLR behavior in this scenario.If thing is compiled with /dynamicbase on, and you have 64 bit windows, you essentially have proper ASLR.The locations of the heap, stack, Process Environment Block, and Thread Environment Block are also randomized. A security whitepaper from Symantec noted that ASLR in 32-bit Windows Vista may not be as robust as expected, and Microsoft has acknowledged a weakness in its implementation.[32]
And Windows Vista in 2007 had already kernel level ASLR.
And btw. Microsoft has settings that certain executables even if they don't have /dynamicbase on, they still have manual overwrite to use mandatory ASLR on them anyway. For example, excel.exe has forced ASLR on, so even if somehow you got executable without /dynamicbase on, it would still work as if it is on by default.
Comment


Comment