Phoronix: A Complete Look At Spectre V1/V2/V4 & Meltdown
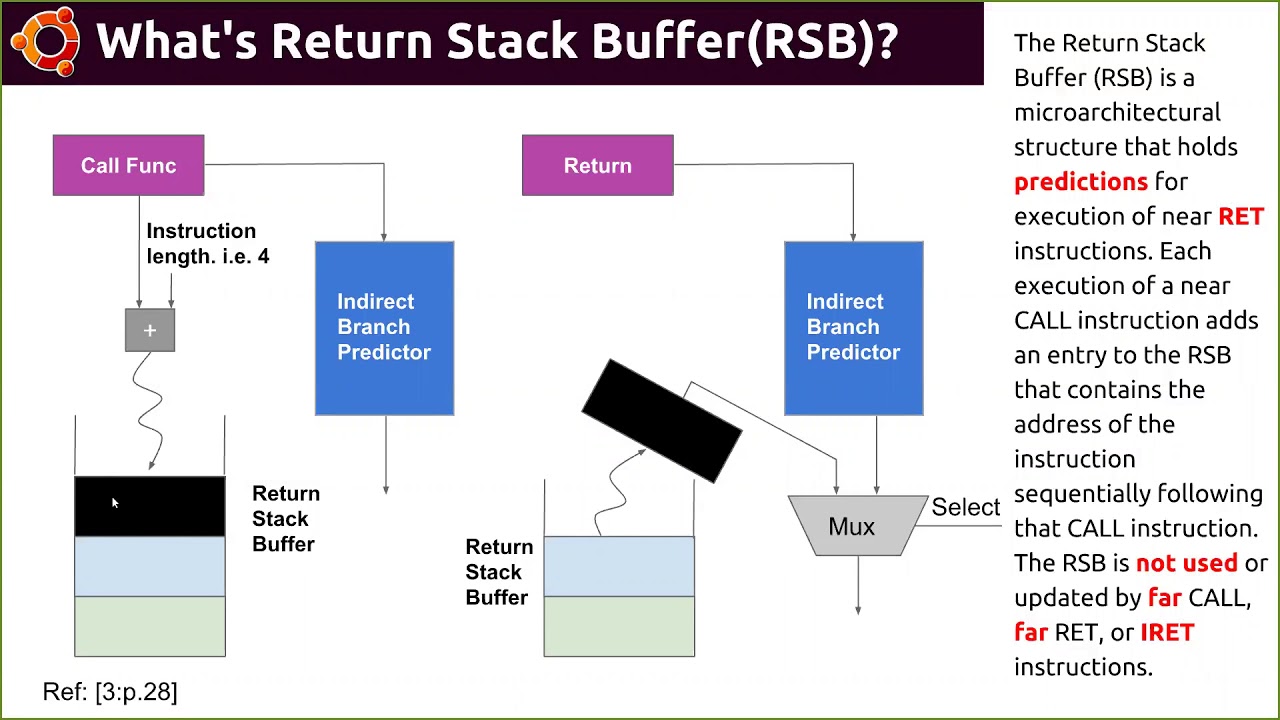
Canonical's Engineering Tech Lead, Gavin Guo, has passed along a big slide deck on a presentation he is preparing about the Spectre and Meltdown CPU vulnerabilities...
Canonical's Engineering Tech Lead, Gavin Guo, has passed along a big slide deck on a presentation he is preparing about the Spectre and Meltdown CPU vulnerabilities...




Comment