Phoronix: Ubuntu 23.10 Adding Experimental TPM-Backed Full Disk Encryption
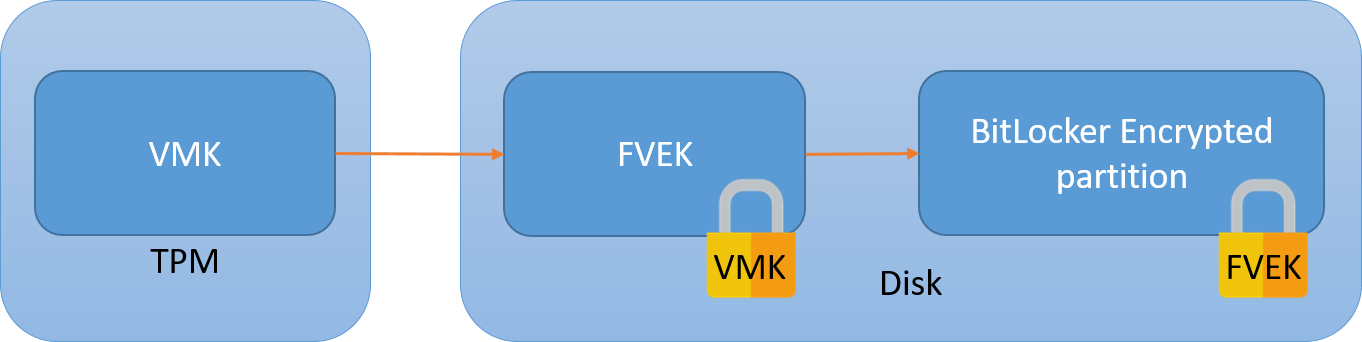
As an experimental feature for next month's Ubuntu 23.10 release, Canonical is introducing initial support for TPM-based full disk encryption to make use of your system's Trusted Platform Module (TPM). The downside though is this extra security relies on Snaps, including for the kernel and GRUB bootloader...
As an experimental feature for next month's Ubuntu 23.10 release, Canonical is introducing initial support for TPM-based full disk encryption to make use of your system's Trusted Platform Module (TPM). The downside though is this extra security relies on Snaps, including for the kernel and GRUB bootloader...



Comment