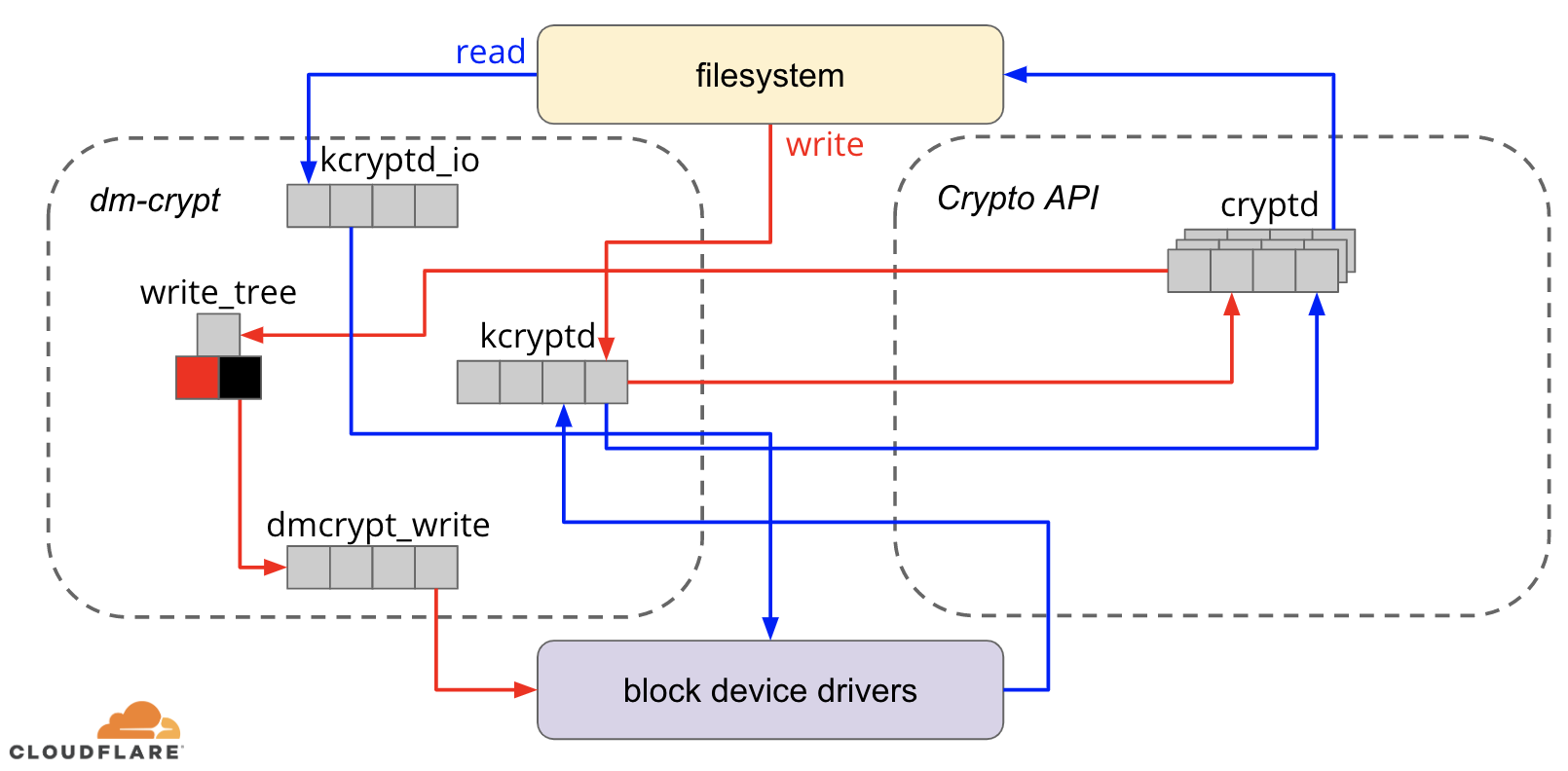
Zen3 scored impressive gains as well, even though it doesn't feature AVX512. While Zen2 fares much worse.
And Sapphire Roads results for avx2 and both avx10 flavours are very close.
All there processors feature AVX2, but only some have high gains. Also AVX512 is again not so much faster than AVX2.
So its VAES that is mosty responsible for this huge uplift, not AVX.
And Sapphire Roads results for avx2 and both avx10 flavours are very close.
All there processors feature AVX2, but only some have high gains. Also AVX512 is again not so much faster than AVX2.
So its VAES that is mosty responsible for this huge uplift, not AVX.


Comment